Table of Contents
- Purpose of this Q and A type document
- 1. Security Framework
- 2. Internet Applications
- 3. Application Architecture
- 4. Security Infrastructure
- 5. Security Technology
- 6. Network Security
- 7. Attacks
- 8. Application Server
- 9. Reliability and Availability
- 10. Secure Computing: Access control lists vs. capabilities
- 11. Common Risks
The purpose of this list is to check and enhance the awareness for security problems e.g. in web applications. It is the interplay of security technologies that is important - driven by a security framework that defines policies and strategies.
Of course knowledge about specific security technologies is needed as well, so the questions go from more complex ones which offer opportunities for design discussions to simpler ones which cover specific technologies.
I would like to thank Rüdiger Gunreben for contributing to this list.
Certain basic attitudes towards security risks exist: Risk denial (head in the sand), risk avoidance and risk as a business opportunity ("Risk is where the money is" the famous paper by Dan Geer)
A security policy defines a companies attitude towards security. Its importance lies in the fact that it has legal ramifications for everybody working in the company.
- 1. A city wants to change its administration into a virtual counter. Passport requests, change of location etc. can be performed via Internet. What would you put into the security policy for this city?
- 2. Given the e-government example from above, define a data classification scheme for different data types and associate IT-practices and rules with each type.
In many cases these guidelines are too abstract to be useful. Here we want to make them better understandable by embedding them in real-world examples.
- 1. You are the system administrator of a large application host. A developer requests superuser rights on this machine to run some tools. Your options are to either hand over the root password, create the users id and associate it with a superuser group or create a userid and a special program that gives selected access to system tools. Discuss this scenario with respect to the basic security guidelines.
- 2. How can you protect your company from buffer overlow attacks? What basic security guideline might be helpful here?
- 3. A company allows managers to increase the rights of sub-ordinates by changing entries in an authorization DB. No actions are required by the subordinates - besides asking their managers for those rights. Is this a safe process? Who might be at risk here?
| 1. | You are the system administrator of a large application host. A developer requests superuser rights on this machine to run some tools. Your options are to either hand over the root password, create the users id and associate it with a superuser group or create a userid and a special program that gives selected access to system tools. Discuss this scenario with respect to the basic security guidelines. TipWhat are the basic rules for access to resources? If access is allowed, in which way is it constrained and documented? |
Access to data or functions should be guided by the need-to-know and need-to-do principle (give only so much authorization that a person can do exactly what she needs to do) and the principle of mandatory authentication of the real user (no functional user ids) These principles applied to our example lead to the following judgement:
| |
| 2. | How can you protect your company from buffer overlow attacks? What basic security guideline might be helpful here? TipDo not assume that a computer cannot be broken into. |
You should have learned that there is no real protection from buffer overflow attacks because new ones pop up almost daily. Your security measures comprise the following:
| |
| 3. | A company allows managers to increase the rights of sub-ordinates by changing entries in an authorization DB. No actions are required by the subordinates - besides asking their managers for those rights. Is this a safe process? Who might be at risk here? TipEver heard about that horse that was left as a gift to the trojans? |
This process has two security problems:
|
Frequently a company acquires new applications (or develops those) which will provide a service on the internet. This section deals with the problem of performing a security analysis on a web application.
| 1. | Your company is selling bikes and has recently bought a web shop application. What kind of questions would you ask the application provider before giving an OK to run the application service? TipThink about administration, security technology, integration into the company environment and maintenance. |
Table of Contents
Abstract
Such an internet service is very interesting for two reasons: the online ticket itself is a security problem because of the problem of abuse (copy etc.). The ticket processing application deals with confidential user data and includes a purchase process - both critical features with respect to security. The following discusses design aspects of such an application
The DB online ticket contains two rows of crypto data called "Zertifikate", the travel information (from/to) and the travelers name. Some other inter-application keys and identifiers are provided which seem to be unrelated to the problem of ticket verification and cancellation. Each ticket is valid for a couple of days and travellers can change to other trains on different times (they might lose their reservations but the tickets stay valid). Conductors invalidate tickets by placing a stamp on the ticket. They verify tickets by running the travellers BahnCard through their mobile terminals, enter information from the online ticket and compare results with the ticket.
- 1. What are possible abuses of this system, given the constraints from above? Be creative and think about how you could re-use tickets, try false re-embursements etc.
- 2. Design a system that prevents ticket abuse
| 1. | What are possible abuses of this system, given the constraints from above? Be creative and think about how you could re-use tickets, try false re-embursements etc. |
| 2. | Design a system that prevents ticket abuse TipThink about crypto mechanisms you could use. What else might you need to prevent abuse? What role plays the mobile terminal? What role plays the bahncard? |
Note
The DB application collects user data (Bahncard, credit card etc.) and performs a purchase process. The initial travel information (from/to) is collected in http mode, user personal data are transmitted via https. A userid/password based login is created using https.
- 1. Are user data collected safely using the above mechanism? Is there a window for abuse?
- 2. You might have decided to use the bahncard as the main user identifier in your application, like a primary key which holds all user related informatin together. You were also assuming that the bahncard is always personal and not a shared item. Now the bahn tells you that they would like to offer companies a way to book online tickets against a company bahncard. How does this affect your design of the online ticket security? What does this mean for your payment process where you have until now always deducted the ticket price from an individual credit card?
- 3. By opening the online ticket service to companies (usually the HR departments) the business process gets changed considerably. Now company DELEGATES perform the purchasing. There might be SEVERAL people involved in those bookings in large companies. How does this affect your authentication and authorization process?
- 4. A web developer from the Deutsche Bahn claims that the online ticket application also provides proof of purchase because it is based on SSL/https. Discuss this statement.
- 5. If a proof of purchase would be needed in the online ticket application, what would you suggest as a possible solution?
- 6. The DB wants to offer this service also from so called "kiosk" systems. These systems are computers placed in public places like shopping malls. They have internet connection and customers can use them to look up travel information and buy tickets which will be printed on the spot. Discuss how this new interface will affect your security assumptions.
- 7. The DB wants another interface supported: WAP enabled mobile phones. Will it have an effect on your security architecture? Why not?
| 1. | Are user data collected safely using the above mechanism? Is there a window for abuse? TipFirst use of the online ticket service requires a user to provide user data and bahncard/credit card information. The ticket is printed right after that. How does the company know that the user really is who he claims to be? | |||
| 2. | You might have decided to use the bahncard as the main user identifier in your application, like a primary key which holds all user related informatin together. You were also assuming that the bahncard is always personal and not a shared item. Now the bahn tells you that they would like to offer companies a way to book online tickets against a company bahncard. How does this affect your design of the online ticket security? What does this mean for your payment process where you have until now always deducted the ticket price from an individual credit card? TipIs there only one company bahncard per company? Many? Many different cards? | |||
| 3. | By opening the online ticket service to companies (usually the HR departments) the business process gets changed considerably. Now company DELEGATES perform the purchasing. There might be SEVERAL people involved in those bookings in large companies. How does this affect your authentication and authorization process? TipThis has to do with so called "mandantenfähigkeit" of an application - feared or ignored by most developers. Let's assume there are five people in an HR department. How would they identify themselves? What information needs to be shared? | |||
| 4. | A web developer from the Deutsche Bahn claims that the online ticket application also provides proof of purchase because it is based on SSL/https. Discuss this statement. TipFrom a cryptography point of view: what must be given to achieve a "proof"? How do you proof a purchase in real life? | |||
A common misconception about SSL/https: It secures the of information as long as it is information in transport. Meaning that the receiver has NOproof whatsoever attached to the bits and bytes that seem to document the purchase. | ||||
| 5. | If a proof of purchase would be needed in the online ticket application, what would you suggest as a possible solution? TipAny possible solution will do. Do not consider feasibility with respect to cost or effort. | |||
| 6. | The DB wants to offer this service also from so called "kiosk" systems. These systems are computers placed in public places like shopping malls. They have internet connection and customers can use them to look up travel information and buy tickets which will be printed on the spot. Discuss how this new interface will affect your security assumptions. TipThink about people walking away while still logged in or with the transaction unfinished. What if somebody looks over your shoulder while the application displays private data? Do you have a login problem now? | |||
Kiosks are public places and suffer mainly from two security risks. First one is the problem of when a session is finished. At any time the customer may decide to leave the kiosk. This means your application needs to take into calculation that from one instant to the next the identity on the other side may have changed or could change. Your assumptions about
all might be wrong in the kiosk situation. Event the way you presented information (e.g. credit-card number to let the customer check if it is still correct) might no longer be appropriate. But the real question is: Do you need to represent location and or situation in your application? And how would this effect your other login/authentication mechanisms? | ||||
| 7. | The DB wants another interface supported: WAP enabled mobile phones. Will it have an effect on your security architecture? Why not? TipWhat technologies did you use to shield your application from changes in authentication mechanisms? | |||
Abstract
Developers do not spend too much time thinking about the business organization (processes and organizations) behind a particular application. A lot of it is security relevant and might have a direct impact on the application.
Abstract
A lot of internet applications deal with credit cards for ordering shop items, booking of events or transportation etc. Running a web shop requires a contract with a credit card company. These companies usually require a certain quality of processing applied to the credit card information.
Note
You are running a web shop which accepts credit cards. After applying at VISA as a dealership you receive a questionaire from VISA where the credit card company asks you a lot of questions about how you process the credit card information.
- 1. Design a questionaire which will be used by VISA to check if companies deal with credit card information securely. What kind of information system security etc. VISA might be interested in? Think about how the credit card information enters your system, who gets access to it, how it is validated (if at all) etc.
- 2. Design a software system that protects credit card information from the point of entry over processing to long term storage. Show how you handle access, transport and storage of this information.
| 1. | Design a questionaire which will be used by VISA to check if companies deal with credit card information securely. What kind of information system security etc. VISA might be interested in? TipThink about how the credit card information enters your system, who gets access to it, how it is validated (if at all) etc.
|
Here are some parts of the visa questionaire. Enjoy.   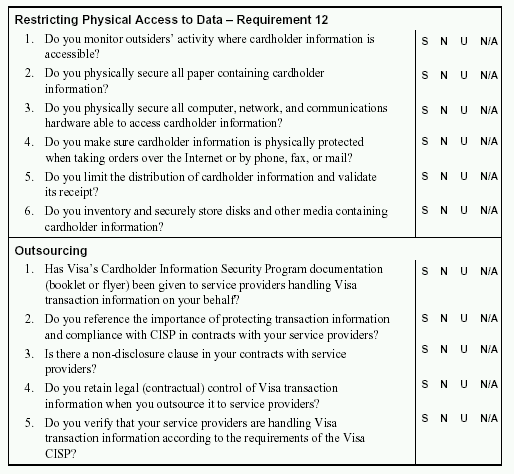
| |
| 2. | Design a software system that protects credit card information from the point of entry over processing to long term storage. Show how you handle access, transport and storage of this information. TipYou can come up with a data classification schema and associate the required processing rules and policies with the level for credit card information. |
Abstract
Security Issues in designing a secure messaging system for customer-company communication. Differences between various messaging systems with respect to confidentiality, integrity and non-repudiation.
Note
Your company does software development in the internet area. A client approaches you with the follwing problem and asks you for a proposal.
The customer wants to improve the electronic communication with its clients. Currently some clients know the e-mail addresses of employees and send orders (e.g. to buy or sell shares) via e-mail.
- 1. E-mail based business processes with clients can pose certain security problems. In this case clients send credit card and account numbers and place orders. Please write down a number of possible problems.
- 2. Define a security policy for the business process of exchanging messages with clients that contain orders and personal data.
- 3. Security properties of e-mail. Make a list of these properties using the usual security terms: authentication, authorization, integrity, confidentiality and non-repudiation. Is that all? How about availability? Does availability play a role in the business process above?
- 4. How could the security of the business process from above be improved while still using e-mail? Define an infrastructure for secure e-mail.
- 5. Design an alternative solution which uses a database to hold messages from and to clients. Which protocols would you use? Don't forget authentication and the other security requirements.
| 1. | E-mail based business processes with clients can pose certain security problems. In this case clients send credit card and account numbers and place orders. Please write down a number of possible problems. TipThink about the kind of data that might get transmitted and who sends/receives what information. |
| 2. | Define a security policy for the business process of exchanging messages with clients that contain orders and personal data. TipYou need to think about who receives messages (a person or a group) and how these should be processed (responsibilities, authorizations etc. |
| 3. | Security properties of e-mail. Make a list of these properties using the usual security terms: authentication, authorization, integrity, confidentiality and non-repudiation. Is that all? How about availability? Does availability play a role in the business process above? |
| 4. | How could the security of the business process from above be improved while still using e-mail? Define an infrastructure for secure e-mail. TipWrite down what the technical requirements for such a solution are. |
| 5. | Design an alternative solution which uses a database to hold messages from and to clients. Which protocols would you use? Don't forget authentication and the other security requirements. |
Table of Contents
A main feature of modern application architecture is the separation of security definitions from business code. The following questions want to provide the rationale behind this architectural decision.
A request typically flows from a client station through web intermediates (proxies etc.) to a web container and from there e.g. to an EJB application server. The identity used throughout this request might change. Delegation of security information is unfortunately both complicated and diverse.
Table of Contents
Packet filters (both stateless and stateful) and Bastion Hosts are types of firewalls. Here we want to understand their proper use depending on context and requirements.
- 1. What is the main difference between a stateless and a stateful packet filter?
- 2. A company wants to restrict the number of requests to a certain service from each client. Do they use a stateful or a stateless packet filter for that purpose?
- 3. A company wants to filter packets depending on the content, e.g. prevent web access to some sites. Do they use a stateful or a stateless packet filter for that purpose?
- 4. A company wants to authenticate requests before letting them enter or leave. What kind of firewall can be used for that? Explain why
- 5. What is the basic advantage of a network firewall - derived from its location between intranet and internet.
- 6. What is the basic advantage of a network personal firewall - derived from its location on individual machines.
- 7. The concept of "network edge" firewall is fascinating because it solves basic problems of network firewalls as well as of personal firewalls. Please elaborate on what these problems are.
| 1. | What is the main difference between a stateless and a stateful packet filter? |
| 2. | A company wants to restrict the number of requests to a certain service from each client. Do they use a stateful or a stateless packet filter for that purpose? |
| 3. | A company wants to filter packets depending on the content, e.g. prevent web access to some sites. Do they use a stateful or a stateless packet filter for that purpose? |
| 4. | A company wants to authenticate requests before letting them enter or leave. What kind of firewall can be used for that? Explain why |
| 5. | What is the basic advantage of a network firewall - derived from its location between intranet and internet. |
| 6. | What is the basic advantage of a network personal firewall - derived from its location on individual machines. |
| 7. | The concept of "network edge" firewall is fascinating because it solves basic problems of network firewalls as well as of personal firewalls. Please elaborate on what these problems are. TipIn case of network firewalls you should think about the topology and location of those firewalls and what happens to the rules if the intranet grows. In case of the personal firewalls you should think about the ground these software firewalls operate on. |
This section goes into the details of filtering rules for firewalls. Besides its trusted computing base a firewall finally is only a filter
- 1. Filtering rules depend on the company policy with respect to internet access and internet services provided. Design a policy for a typical company comprising web access, ftp, telnet, mail access, news, real-audio, chat etc.
- 2. What are the main network elements that can be used in firewall filtering?
- 3. You find the following rule in a firewall script (IPTABLES): $IPTABLES -A FORWARD -s $INTRANET -d $ANY -m - -state NEW,ESTABLISHED,RELATED -j ACCEPT. What does this statement mean and what security policy is expressed by it?
- 4. How trustworthy are the main network elements that can be used in firewall filtering?
- 5. Define a ruleset (e.g.for iptables or ipchains) that allows all intranet hosts access to standard web servers on the internet except to site 11.12.13.14 which is a known internet gambling site.
- 6. Leading commercial firewalls are almost completely based on the application gateway concept. Give reasons for this tendency and discuss advantages/disadvantages of application gateways
- 7. Why is it hard to detect or log the end of a UDP session?
- 8. On a masquerading firewall with 2 network cards, where would you log the intranet traffic to the internet? On the inranet network card or the internet network card?
- 9. Why should you allocate a separate partition for the /var/log directory on a linux software firewall?
| 1. | Filtering rules depend on the company policy with respect to internet access and internet services provided. Design a policy for a typical company comprising web access, ftp, telnet, mail access, news, real-audio, chat etc. TipFor every service (you can use others as well) tell in which direction it is allowed. You might want to disallow some completely. Explain. |
| 2. | What are the main network elements that can be used in firewall filtering? TipThink about the packet structures of the TCP/IP/ICMP protocol stack |
| 3. | You find the following rule in a firewall script (IPTABLES): $IPTABLES -A FORWARD -s $INTRANET -d $ANY -m - -state NEW,ESTABLISHED,RELATED -j ACCEPT. What does this statement mean and what security policy is expressed by it? TipThink about who gets permission for what and define the scope of this permission. |
| 4. | How trustworthy are the main network elements that can be used in firewall filtering? TipThink about spoofing network packets |
| 5. | Define a ruleset (e.g.for iptables or ipchains) that allows all intranet hosts access to standard web servers on the internet except to site 11.12.13.14 which is a known internet gambling site. TipThink about the order of your rules. You can use any symbolic notation - it need not be iptables or ipchains. |
| 6. | Leading commercial firewalls are almost completely based on the application gateway concept. Give reasons for this tendency and discuss advantages/disadvantages of application gateways TipThink about kernel/user space solutions and performance |
Proxy based solutions are more powerful with respect to protocol detection, content analysis and authentication support. And they separate internal and external network physically which means that no open channel is accidentially missed. Every channel to the outside needs to have a proxy server installed to work at all. | |
| 7. | Why is it hard to detect or log the end of a UDP session? |
UDP is a sessionless protocol. This means that it is the application that may treat a number of UDP requests and responses as a session but this is not visible in the network packets, e.g. through sequence counters etc. TCP e.g. uses special close commands to tell the other side about the end of a session. | |
| 8. | On a masquerading firewall with 2 network cards, where would you log the intranet traffic to the internet? On the inranet network card or the internet network card? TipFirewalls usually have two network cards, one attached to the intranet, the other one attached to the internet. Those firewalls are also used to masqueradeintranet addresses. Masquerading means hiding the addresses of the internal network |
On the intranet side so you can see the unmasked (not masqueraded addresses) of the real intranet hosts. Later on they will be replaced through the IP address of the firewall. | |
| 9. | Why should you allocate a separate partition for the /var/log directory on a linux software firewall? TipThink about what goes into the /var/log space! |
A Denial-of-service (DOS) attack against the firewall would probably create huge log files which should not fill up important file system space (e.g where the system itself lives) and kill the firewall itself. |
- 1. A companies security policy does not allow direct connections from the internet to the intranet or vice versa. The company wants to run a web server with static html pages. Design a DMZ that can handle these requirements.
- 2. Design a DMZ that forces some services through a bastion host but lets others connect directly to the internet.
| 1. | A companies security policy does not allow direct connections from the internet to the intranet or vice versa. The company wants to run a web server with static html pages. Design a DMZ that can handle these requirements. |
| 2. | Design a DMZ that forces some services through a bastion host but lets others connect directly to the internet. |
The typical sandwich design of a DMZ gives you a lot of freedom with respect to routing requests. The packet filters can force packets to the bastion host (possibly using source nat) while letting others go through directly. |
Abstract
Services over the internet are a standard security topic. We will discuss service properties and their security consequences in this section.
Note
Imagine you are the responsible person for internet security in this company
- 1. Somebody wants to run a certain service between intranet and internet. What are you going to ask about this service? Discuss the possible answers and how you would decide about the services use.
- 2. Security properties of internet services. Write down service properties that are relevant for security. Think about properties that make it easy to control and filter a service. How will firewalls deal with it? How can its use be controlled in the intranet? What kind of data or commands are possible?
- 3. How dangerous are the following services: FTP, Telnet, WWW, RPC, NFS, Mail. Start with the usual security topics (authentication etc.) and after that ask about firewalls, data and control channels.
| 1. | Somebody wants to run a certain service between intranet and internet. What are you going to ask about this service? Discuss the possible answers and how you would decide about the services use. |
| 2. | Security properties of internet services. Write down service properties that are relevant for security. TipThink about properties that make it easy to control and filter a service. How will firewalls deal with it? How can its use be controlled in the intranet? What kind of data or commands are possible? |
| 3. | How dangerous are the following services: FTP, Telnet, WWW, RPC, NFS, Mail. TipStart with the usual security topics (authentication etc.) and after that ask about firewalls, data and control channels. |
VPNs use a very low level in the protocol stack to securely transmit information. We will discuss some consequences of this approach.
- 1. What is the main problem of link-level encryption?
- 2. One of your suppliers offers you to create a VPN between both companies. What might make you think twice about that proposal?
| 1. | What is the main problem of link-level encryption? TipDo you remember the "end-to-end argument" in security? Why did it claim that the closer the security is to the application, the safer it is? Think about which ways packets sometimes need to travel |
The routing is the weak point. Within the routers those packets are not encrypted and available to attack. This boils down to the fact that the security is in the channel and not on the object. | |
| 2. | One of your suppliers offers you to create a VPN between both companies. What might make you think twice about that proposal? |
A VPN really links networks. In other words unsafe protocols like windows networking etc. could cross domains easily when connected through VPNs. The other VPN really becomes part of your network. There is no border between both companies. It raises a trust issue. |
Table of Contents
This chapter discusses problems related to specific security technologies.
Biological ways of user authentication are supposedly very reliable. Recent studies have shown that e.g. fingerprint identification is much less reliable than what was previously believed.
- 1. Companies have spent a lot of money on fingerprint scanners etc. If a simple rubber finger for 10$ can fool expensive fingerprint scanners, what are the consequences for companies using such equipment? Think about the believe in technology those companies must have.
- 2. What are the possible consequences for an employee whose fingerprint has been faked?
| 1. | Companies have spent a lot of money on fingerprint scanners etc. If a simple rubber finger for 10$ can fool expensive fingerprint scanners, what are the consequences for companies using such equipment? TipThink about the believe in technology those companies must have. |
| 2. | What are the possible consequences for an employee whose fingerprint has been faked? |
Nowadays a secure channel on the Internet is almost always implemented using Secure Socket Layer (SSL) Unfortunately a lot of misconceptions exist about the security associated with the use of SSL. This section is supposed to set things straight.
- 1. Is it true that with an SSL session client and server are always securely authenticated? Discuss.
- 2. Is it true that with an SSL session client and server data are transmitted with confidentiality and integrity guaranteed? Discuss.
- 3. Is it true that with an SSL session a client always knows who she is talking to? Discuss.
- 4. Is it true that with an SSL session man-in-the-middle attacks are no longer possible? Discuss.
- 5. Why does SSL use symmetric keys to transmit bulk data? Discuss.
- 6. List uses which do not fit well to the channel oriented design of SSL.
| 1. | Is it true that with an SSL session client and server are always securely authenticated? Discuss. |
| 2. | Is it true that with an SSL session client and server data are transmitted with confidentiality and integrity guaranteed? Discuss. |
| 3. | Is it true that with an SSL session a client always knows who she is talking to? Discuss. |
| 4. | Is it true that with an SSL session man-in-the-middle attacks are no longer possible? Discuss. |
| 5. | Why does SSL use symmetric keys to transmit bulk data? Discuss. |
| 6. | List uses which do not fit well to the channel oriented design of SSL. |
- 1. What is the main difference between http and e-mail?
- 2. Which one of the main security qualities: integrity, confidentiality and non-repudiation can NOT be provided by a secure channel?
| 1. | What is the main difference between http and e-mail? |
| 2. | Which one of the main security qualities: integrity, confidentiality and non-repudiation can NOT be provided by a secure channel? |
- 1. What is the worst attack that can happen to a secure channel based session?
- 2. What are the dangers of using a client side public key infrastructure based on certificates? Who is at risk and why?
| 1. | What is the worst attack that can happen to a secure channel based session? TipYou need to think about what is really secured by a secure channel: each message that goes across the wire or a connection/session between two parties? |
| 2. | What are the dangers of using a client side public key infrastructure based on certificates? Who is at risk and why? TipThink about the worst case scenario for a public key crypto system and how it could happen. |
Table of Contents
Abstract
An application server environment includes much more than just the application server itself. Many components interact to process a request. Security between components is a major issue here.
- 1. Draw a diagram that shows a complete infrastructure forming a so called "Distributed Trusted Computing Base" for a web application.
- 2. How are the customer data secured across all components?
- 3. Individual components should authenticate themselves against each other? If you use certificates, where do you use official certificates and where self-signed certificates?
- 4. You want to authenticate the web server against the application server and vice versa. Explain the process of creating and exchanging certificates to achieve mutual authentication.
- 5. Private Keys stored in keystores are a security problem. They are protected by so called passphrases which control access to the keystore and use of the private key. Istn't this just moving the problem to a different place (the passphrase)? How is the passphrase protected?
- 6. If the concept of stash files does not really convince you - would you know an even better place to store your private key (or the private key of an important server)?
| 1. | Draw a diagram that shows a complete infrastructure forming a so called "Distributed Trusted Computing Base" for a web application. TipStart with a request from the client side and let it flow through intermediate components until it reaches backends. Do not forget helper components e.g. for user administration. |
| 2. | How are the customer data secured across all components? |
| 3. | Individual components should authenticate themselves against each other? If you use certificates, where do you use official certificates and where self-signed certificates? |
| 4. | You want to authenticate the web server against the application server and vice versa. Explain the process of creating and exchanging certificates to achieve mutual authentication. TipThink about the two sections in a keystore |
| 5. | Private Keys stored in keystores are a security problem. They are protected by so called passphrases which control access to the keystore and use of the private key. Istn't this just moving the problem to a different place (the passphrase)? How is the passphrase protected? TipThink about the concept of stash files |
| 6. | If the concept of stash files does not really convince you - would you know an even better place to store your private key (or the private key of an important server)? TipSomebody once said that internet security is like using an armoured tank to transport information between somebody who lives in a garden to somebody who lives on a park bench. What is the fundamental problem with storing this information on a host? |
- 1. XML provides the so called "entity" feature which is a macro definition who's location an be specified using a URL. Parsers will typically go and fetch the macro source automatically. Some web sites offer translation services where one can send a xml document and retrieve a transformed version. Can the entity mechanism be abused in those cases? What could it be used for?
- 2. XSLT processors offer escape functions to call other languages, e.g. Java or Java script. Those processors are frequently run within a servlet context on web servers. Discuss possible security problems.
- 3. XSLT is a stylesheet language that uses XML as its format.Somebody sends you an XSLT stylesheet which gets executed on your system. Discuss possible security problems.
- 4. Discuss the difference between security policy and mechanism using authentication as an example.
| 1. | XML provides the so called "entity" feature which is a macro definition who's location an be specified using a URL. Parsers will typically go and fetch the macro source automatically. Some web sites offer translation services where one can send a xml document and retrieve a transformed version. Can the entity mechanism be abused in those cases? What could it be used for? TipThink about the number of possible references or where these references may point (local, remote) |
| 2. | XSLT processors offer escape functions to call other languages, e.g. Java or Java script. Those processors are frequently run within a servlet context on web servers. Discuss possible security problems. |
| 3. | XSLT is a stylesheet language that uses XML as its format.Somebody sends you an XSLT stylesheet which gets executed on your system. Discuss possible security problems. TipXSLT is a turing complete language with accessor functions to peripheral information |
| 4. | Discuss the difference between security policy and mechanism using authentication as an example. |
Table of Contents
Security is more than just keeping things secret or regulating access to resources. Often it includes guarantees about business procedures and the availability of services to do business. Just like backup and restore procedures are also part of security.
The way a business procedure or protocol is designed affects its reliability a lot. There was this company that organizes one of the worlds largest trade-shows. To allow exhibitors to book places on their trade show they installed the following procedure: Exhibitors could request a form and send it via fax back to the trade-show organizer which reserved the place and collected the money later on.
A few days before the big show started a number of companies showed up to set up their displays at their reserved spots - only that those spots had been given to other companies and nobody at the organizer new a thing about these reservations. The companies without spaces waved confirmation protocols from their fax machines saying "successfully sent xxx pages".
It turned out that fax machines sometimes do not follow the fax protocol and that on the receiving side there seems to be no transactional behavior in many cases: Sometimes sender faxes get an acknowledgement even though the receiver had problems receiving the document or the receiver crashed after receiving the document,(right after confirming it) but had not made it persistent yet.
| 1. | How would you design this business protocol to avoid such unpleasant situations? TipNo need to get deep into IT technology (distributed transactions etc.) |
Have the organizer state the simple policy on each and every form: Do not assume place reservation without written confirmation through the organizing company. Wait no longer than a week for confirmation then send your booking again. No bookings later than one month before the trade-show begins. |
Table of Contents
- 1. You have developed a very popular program which you want to distribute through various sites to avoid being overrun. There are different possibilities to distribute the source code or binaries: require that all sites use SSL to downloaddigitally sign your code/binaries Discuss the problems with each approach. What do both methods guarantee?
- 2. In the above example you have decided to use digital signatures. What exactly do they guarantee? Do they protect users from running malicious code?
- 3. One of your signed code packages had a security related bug. You've fixed it and now you want to ship a new signed package. What's the problem for your users?
| 1. | You have developed a very popular program which you want to distribute through various sites to avoid being overrun. There are different possibilities to distribute the source code or binaries:
Discuss the problems with each approach. What do both methods guarantee? | ||
| 2. | In the above example you have decided to use digital signatures. What exactly do they guarantee? Do they protect users from running malicious code? | ||
| 3. | One of your signed code packages had a security related bug. You've fixed it and now you want to ship a new signed package. What's the problem for your users? |
Table of Contents
| 1. | A piece from Bruce Schneier: Some companies ask you for your birthdate when you register. In case you forgot your password they ask for your birthdate and if it matches they reset your password. And if you log in on your birthdate there personalized homepage shows "Happy Birthday userxxx". |
Discuss the security problems behind both behaviors. Tiphttp://www.oreillynet.com/pub/wlg/2597 |