Polaris - an ACL restricting Sandbox
What if code follows the ACL pattern, users have ample rights (actually work mostly as admins) and resources cannot be tagged with special protections (besides a few absolutely essential system files which ARE protected by the operating system in a special way...)? Such is the situation on windows.
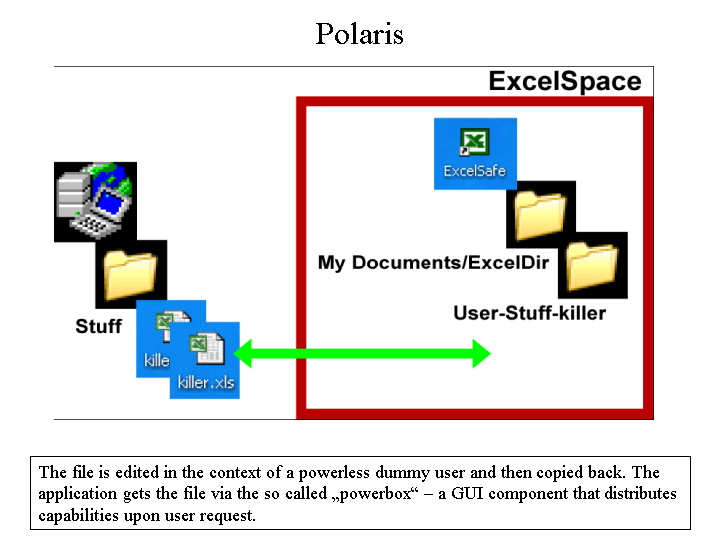
Polaris by Combex provides a safe sandbox to run e.g. Microsoft Office programs in. For this purpose a special user with almost no rights is constructed. Then the file-to-be-edited is copied into the user space of this user and the offica application is started - with macros enabled. At the end of the editing the file is copied back into the space of the real user. Macros in this file may have corrupted it but they could not do any further harm to the users files or the system. The rights of the "dummy" user where just too powerless.
Please note that this sandbox does simply filter the users rights until only the one really needed is handed over to the application (via the dummy user rights).
See: Polaris: Toward Virus Safe Computing for Windows XP,Marc Stiegler, Alan H. Karp, Ka-Ping Yee1, Mark Miller2, Hewlett-Packard Laboratories Palo Alto, California




